Description
full-scale testing effective presentation
System Introduction
Tian-Tep Intrusion Detection and Management System (IDS: Intrusion Detection and managerment Systems) is the first system of its kind in the world.Qixinghen (Chinese company name)Self-developed threat detection products, its main role includes the following aspects:
- Quantifying the threat: discovering, logging, counting and analyzing in real time the network'ssuretyEvents;
- Locating the threat: Combining address location and other means to determine the source of the threat;
- Operational guidance: Provide users with detailed, actionable guidance on incident handling to guide them in making adjustmentsnetwork securityStrategies and means of protection;
- Effectiveness evaluation: At the same time, through the analysis of historical data, the overall level of network security can be examined and the effectiveness of security construction can be measured.
Since 2002, TianTep Intrusion Detection and Management System has been ranked as the top intrusion detection sub-market share in China's IT security market for 19 consecutive years, and it is the No.1 brand of intrusion detection products in China.
Functional Features:
- bypass deployment
T-TranSwitch intrusion detection and management system bypasses the network and does not affect the normal communication of business data when detecting real-time network data streams.
- Intrusion detection
Tin-Tep Intrusion Detection and Management System can detect all kinds of malicious and suspicious behaviors and provide corresponding treatment suggestions:
- threat management
TianTep Intrusion Detection and Management System provides detection of abnormal traffic, which can detect abnormal traffic behavior in real time; it provides IP localization system for intrusion threat events, which can quickly locate the source of the threat.
TianTep Intrusion Detection and Management System also provides independently deployable report analysis components, built-in nearly 100 kinds of report templates, but also according to user needs, the combination of their own report types.
Technical characteristics:
- full-scale testing
- Comprehensive protocol analysis: T-Tep Intrusion Detection and Management System supports protocol self-identification and protocol plug-in technology, which can accurately identify protocols with unconventional ports and new protocols.
- Comprehensive Detection Mechanism: TianTian intrusion detection and management system supports both feature-based and principle-based detection methods, expanding the scope of identifiable detection on the basis of guaranteeing detection accuracy.
- Comprehensive event analysis: Qisda has a set of the industry's most complete support system for follow-up services to ensure fast and accurate response to new events, in addition to providing high-end users with customized event interfaces to perfect customized customer needs.
- Comprehensive Detection Scope: Known Threat Detection and Threat Detection in One
- Comprehensive Detection Performance: T-TranSwitch Intrusion Detection and Management System adopts the shortest time priority algorithm to ensure the detection efficiency of the product in the case of high network data load, which can meet the detection requirements of 100Gb, 1Gb and 10Gb network environment.
- effective presentation
- Accurate Alarm Information: T-TranSwitch Intrusion Detection and Management System incorporates environmental fingerprinting technology, which, after detecting an attack, matches the stored environmental information twice, presenting those alarms that can be confidently considered as "useful" individually, reducing the user's consumption of analyzing operations.
- Detailed information presentation: The alarm information of TianTep Intrusion Detection and Management System includes not only the addresses and protocols of the two parties of the event, but also specific descriptions of the event: vulnerability information, patch recommendations, and impact on the system, etc. The most detailed information can be presented to the user. The most detailed event information can be presented to the user.
- Threat address localization: TTMS provides alarm display combined with actual geographic topology. In the case of large-scale deployment, the device topology can be combined with the geographic topology, allowing administrators to intuitively and quickly determine where the threat is.
- Rich report presentation: T-Tep intrusion detection and management system provides analysis reports based on multiple parameters such as time, address, events, etc. Combined with historical analysis data, it can clearly show the development trend of security construction and help consider the level of network security construction.
Typical Applications:
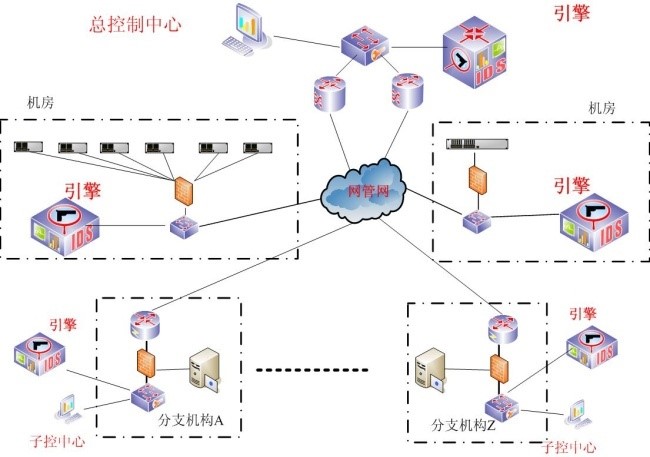
Diagram of single-stage deployment of Tian-Tep

Schematic diagram of Tian-Tep's multi-level distributed deployment
Authoritative Certification:
| serial number | Qualification Name | Awarded by |
| 1 | Computer software copyright registration certificate | PRC State Copyright Administration (SCA) |
| 2 | License for the sale of products dedicated to computer information system security (100 megabytes, gigabytes, 10,000 megabytes) | Ministry of Public Security |
| 3 | Product testing certificate for classified information systems (100 megabytes, gigabytes, 10,000 megabytes) | Security and Confidentiality Evaluation Center for Classified Information Systems of the State Secrets Administration (SSCA) |
| 4 | EAL certification (level 3) (100 Gigabit, Gigabit, 10 Gigabit) | sinoinformation securityassessment center |
| 5 | China National Information Security Product Certification | China Information Security Certification Center (CISCC) |
| 6 | Military Information Security Product Certification (Gigabit Military C), (10 Gigabit Military C) | Chinese People's Liberation Army (PLA) Information Security Evaluation and Certification Center (ISECC) |
| 7 | International CVE Organization Product Compatibility Certification | CVE International Certification Organization |
| 8 | Certificate of independent originality of information security products | China Information Security Evaluation Center (CISEC) |
| 9 | IPV6 Certification | Global IPv6 Test Center |
| 10 | Tian-Tep IDS V7.0 Software Product Registration Certificate | Beijing Municipal Commission of Economy and Information Technology |



Reviews
There are no reviews yet.